Pass The Hash
Understanding the active directory pass the hash attack 2024 Protecting active directory against pass the hash attacks. Pass the hash attack easy network compromisePass the hash toolkit for network security.

Pass The Hash
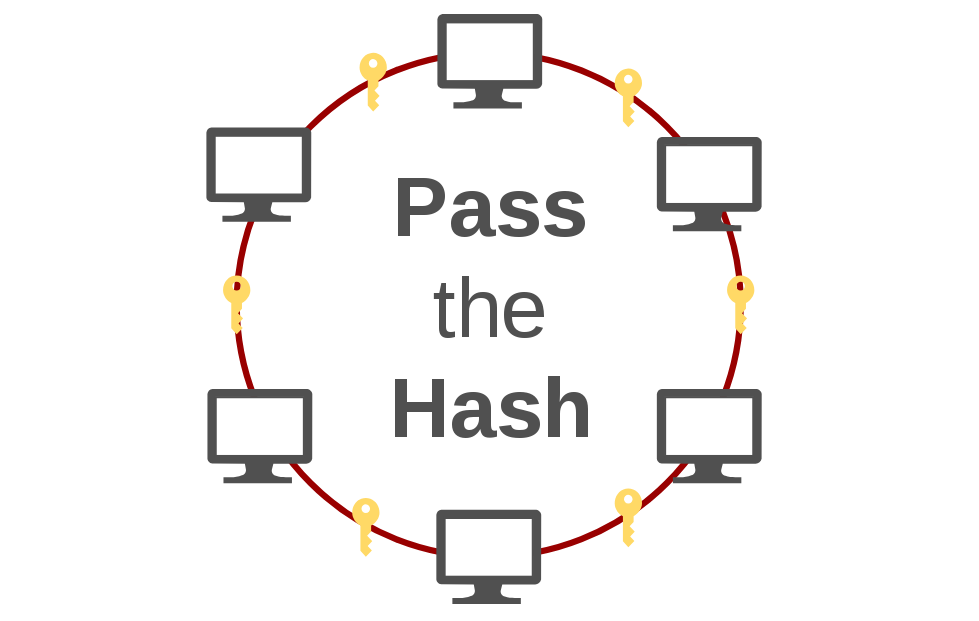
Pass the Hash is a credential theft and lateral movement technique in which an attacker abuses the NTLM authentication protocol to authenticate as a user without ever obtaining the account s plaintext password Pass the hash attack easy network compromise. Pass the hash with mimikatz complete guidePass the hash hackndo.

Understanding The Active Directory Pass The Hash Attack 2024
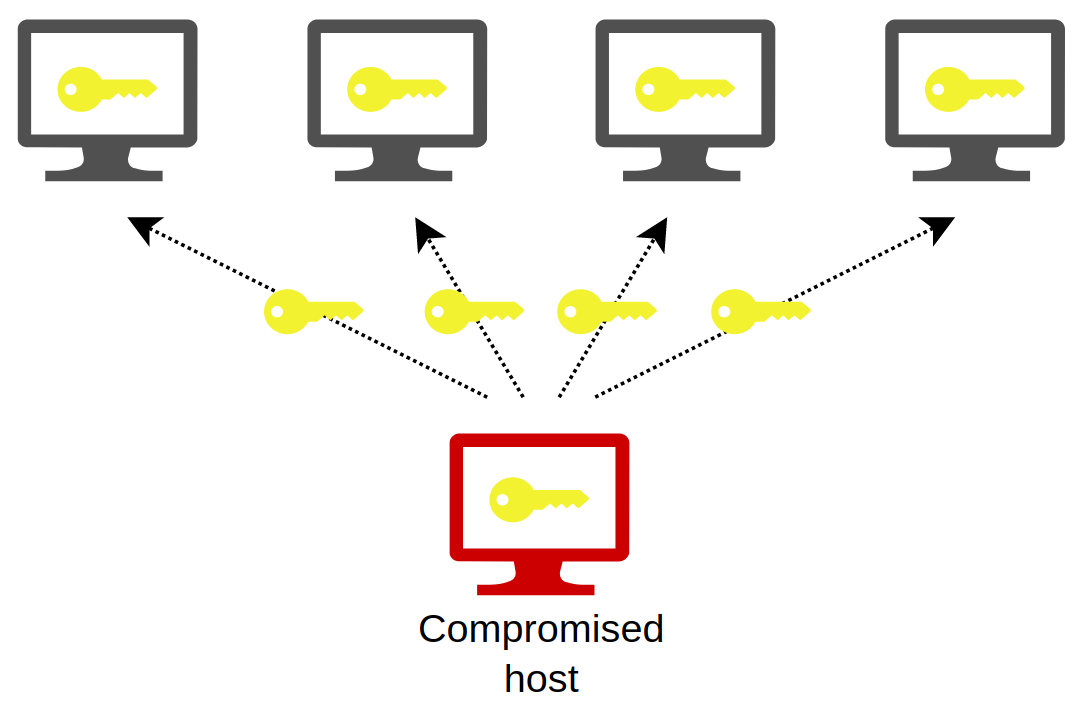
Pass the hash PtH is a method of authenticating as a user without having access to the user s cleartext password This method bypasses standard authentication steps that require a cleartext password moving directly into the portion of the authentication that uses the password hash Jan 22, 2025 · A pass-the-hash (PtH) attack occurs when the cyber attacker steals the hashed user credential or password hash and uses it to deceive an authentication system into generating a new authenticated session on the same network.
Pass The Hash Hackndo
Pass The HashJul 15, 2024 · This document discusses Pass-the-Hash (PtH) attacks against the Windows operating systems and provides holistic planning strategies that, when combined with the Windows security features, will provide a more effective defense against pass-the-hash attacks. In computer security pass the hash is a hacking technique that allows an attacker to authenticate to a remote server or service by using the underlying NTLM or LanMan hash of a user s password instead of requiring the associated plaintext password as is normally the case
Gallery for Pass The Hash
Pass The Hash Hackndo

Protecting Active Directory Against Pass the Hash Attacks

Pass The Hash

Define Pass The Hash Attack Securium Solutions

Pass The Hash Attack Easy Network Compromise

Pass The Hash Attack Easy Network Compromise

Pass The Hash MCSI Library

Pass the Hash Toolkit For Network Security

Detecting Pass the Hash Attacks Blog QOMPLX

Pass the Hash Attacks